Scanning Through The Snow
Overall Thoughts
Today with Try Hack Me’s Advent Of Cyber 2022 event we are looking at NMAP scanning. Overall I feel like this was a good introduction to NMAP and some of its tools. It barely scratched the surface of what I know NMAP is capable of. Although I did feel this was well positioned for the target audience THM was after. Beginners, the people who have never ran an NMAP scan, and thoughs who are starting out.
I really liked how they built off of day 3 and the credientals found during OSINT were incorperated into the challenge.
The Steps
First we need to start the machine we will be scanning and for convience sake I will be using the AttackBox provided by THM.
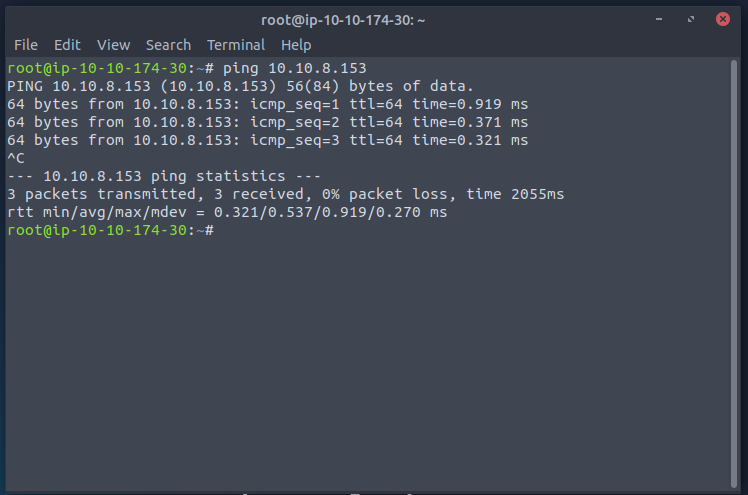
The first thing I like to do is just a ping to make sure the box you are “attacking” with has connection to the target box
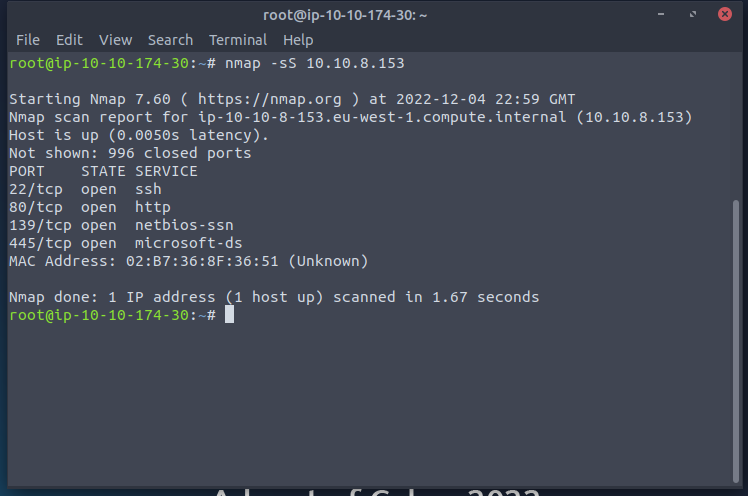
Once I verified that a ping was successfully I followed along in the instructions. The first instruciton I read and completed was a SYN scan. To complete a SYN Scan the -sS flag must be in the command. Please note the IP address should be of your target machine.
1
nmap -sS Ipaddressfortargetmachine
The results form this were
I found four ports open and they are as follows
- Port 22
- Used for SSH
- Port 80
- Used for Http
- Port 139
- Used for Netbios-ssn
- Port 445
- Used for Microsoft-ds
These are all the default for the services that are running on them. After awhile you will learn which port number is normally associated with which service. None of these gave the version or name of the service running on that port so we had to do some more scanning.
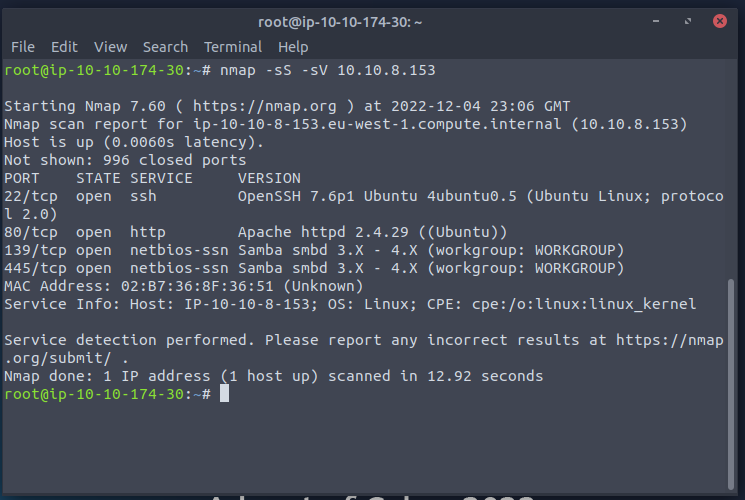
This time we will combine some NMAP flags into one command
1
nmap -sS -sV Ipaddressfortargetmachine
As we learned with the first scan the -sS has NMAP do a SYN scan, -sV tells NMAP to try to figure out the versions of the services running on each port that is open.
These results will allow us to start answering the questions.
Quesiton 1
Form the scan we can see that it is running Apache on port 80
Question 2
From the scan we can see that SSH is running on port 22
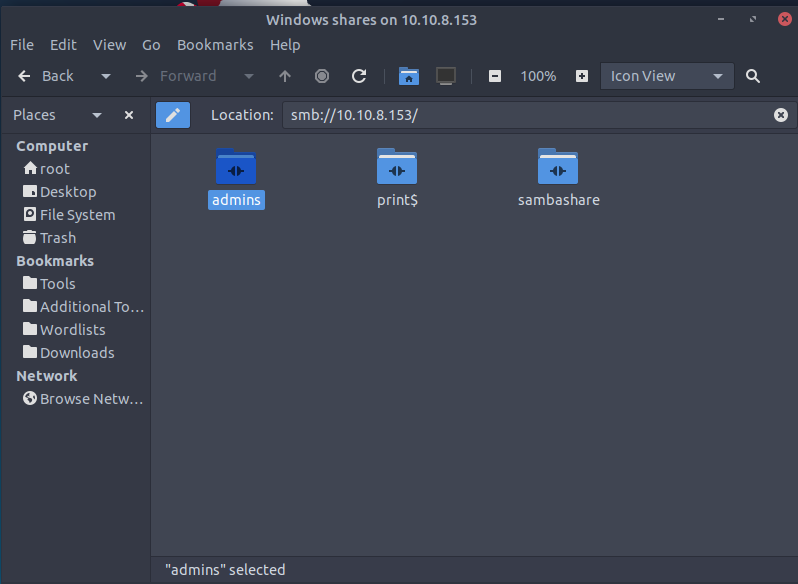
With the first two questions answered we move on, following the instructions, to accessing the samba service we do that by opening our file explorer and connecting to the address. We sould know that samba is available because when we ran the NMAP scan with the -sV flag it returned that samba was running on ports 139 and 445 which are the default ports.
1
smb://Ipaddressfortargetmachine
we get this connection
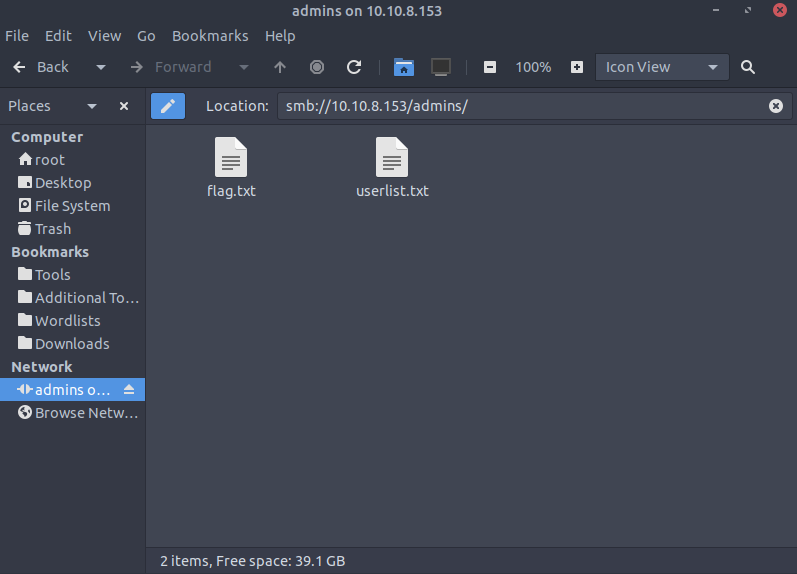
Clicking on the admin folder we get a login prompt. Using the provided login info. Which was found from Day 3 of the challenge we are presented with two files. A flag.txt and userlist.txt
Question 3
Opening the flags.txt file we are presented with the answer to question 3
Question 4
Opening the userlist.txt we are presented with the answer to question 4
That concludes the day 4 challenge of the Advent of Cyber 2022 event. Lets see what tomorrow brings